Written by Lorenzo
Franceschi-Bicchierai
October
20, 2016 // 09:30 AM EST
On March
19 of this year, Hillary Clinton’s campaign chairman John Podesta received an
alarming email that appeared to come from Google.
The
email, however, didn’t come from the internet giant. It was actually an attempt
to hack into his personal account. In fact, the message came from a group of
hackers that security researchers, as well as the US government, believe are
spies working for the Russian government. At the time, however, Podesta didn’t
know any of this, and he clicked on the malicious link contained in the email,
giving hackers access to his account.
Read
more: We Spoke to DNC Hacker 'Guccifer 2.0'
Months
later, on October 9, WikiLeaks began publishing thousands of Podesta’s hacked
emails. Almost everyone immediately pointed the finger at Russia, who is
suspected of being behind a long and sophisticated hacking campaign that has
the apparent goal of influencing the upcoming US elections. But there was no
public evidence proving the same group that targeted the Democratic National Committee was
behind the hack on Podesta—until now.
The data
linking a group of Russian hackers—known as Fancy Bear, APT28, or Sofacy—to the
hack on Podesta is also yet another piece in a growing heap of evidence pointing toward the
Kremlin. And it also shows a clear thread between apparently separate and
independent leaks that have appeared on a website called DC Leaks, such as that
of Colin Powell’s emails; and
the Podesta leak, which was publicized on WikiLeaks.
All these
hacks were done using the same tool: malicious short URLs hidden in fake Gmail
messages. And those URLs, according to a security firm that’s tracked them for
a year, were created with Bitly account linked to a domain under the control of
Fancy Bear.
THE TRAIL
THAT LEADS TO FANCY BEAR
The
phishing email that Podesta received on March 19 contained a URL, created with
the popular Bitly shortening service, pointing to a longer URL that, to an
untrained eye, looked like a Google link.
A
screenshot of the Bitly link used against John Podesta.
Inside
that long URL, there’s a 30-character string that looks like gibberish but is
actually the encoded Gmail address of John Podesta. According to Bitly’s own
statistics, that link, which has never been published, was clicked two times in
March.
That’s
the link that opened Podesta’s account to the hackers, a source close to the
investigation into the hack confirmed to Motherboard.
That link
is only one of almost 9,000 links Fancy Bear used to target almost 4,000
individuals from October 2015 to May 2016. Each one of these URLs contained the
email and name of the actual target. The hackers created them with with two
Bitly accounts in their control, but forgot to set those accounts to private,
according to SecureWorks, a security firm that’s been tracking Fancy Bear for
the last year.
SecureWorks
was tracking known Fancy Bear command and control domains. One of these lead to
a Bitly shortlink, which led to the Bitly account, which led to the thousands
of Bitly URLs that were later connected to a variety of attacks, including on
the Clinton campaign. With this privileged point of view, for example, the
researchers saw Fancy Bear using 213 short links targeting 108 email addresses
on the hillaryclinton.com domain, as the company explained in a somewhat
overlooked report earlier this summer,
and as BuzzFeed reported last week.
Using
Bitly allowed “third parties to see their entire campaign including all their
targets— something you'd want to keep secret,” Tom Finney, a researcher at
SecureWorks, told Motherboard.
It was
one of Fancy Bear’s “gravest mistakes,” as Thomas Rid, a professor at King's
College who has closely studied the case, put it in a new piece published on
Thursday in Esquire, as it gave researchers unprecedented visibility
into the activities of Fancy Bear, linking different parts of its larger
campaign together.
This is
how researchers have been able to find the phishing link that tricked Colin
Powell and got him hacked. This also allowed them to confirm other public
reports of compromises, such as that of William Rinehart, a staffer with
Clinton’s presidential campaign. As The Smoking Gun reported in August,
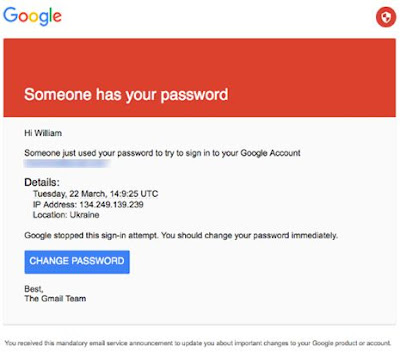
Rinehart received a malicious Google security alert on March 22, according to a
screenshot Rinehart shared with the site. SecureWorks found a URL that had
Rinehart’s Gmail address encoded, which had the same date.
A screenshot of the phishing email received by
Rinehart. (Image: The Smoking Gun)
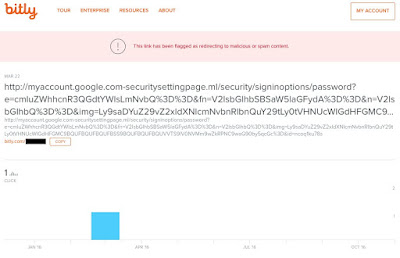
A
screenshot of the malicious Bitly URL received by Rinehart.
Similar
malicious emails and short URLs have also been used recently against
independent journalists from Bellingcat, a website that has investigated the
incident of the shootdown of Malaysian Airlines Flight 17 (MH17) over Ukraine
in 2014, finding evidence that
Russian-backed rebels were behind it.
A
screenshot of a phishing email received by a Bellingcat journalist.
Other
journalists in eastern Europe have also recently been targeted with phishing
emails trying to break into their Gmail accounts.
These
malicious emails, just like the ones used against Podesta, Powell, Rinehart and
many others, looked like Google alerts, and contained the same type of encoded
strings hiding the victims’ names.
It’s unclear why the hackers used the encoded strings, which effectively reveal their targets to anyone. Kyle Ehmke, a threat intelligence researcher at security firm ThreatConnect, argued that “the strings might help them keep track of or better organize their operations, tailor credential harvesting pages to specific victims, monitor the effectiveness of their operations, or diffuse their operations against various targets across several URLs to facilitate continuity should one of the URLs be discovered.”
The use
of popular link shortening services such as Bitly or Tinyurl might have a
simpler explanation. According to Rid, the hackers probably wanted to make sure
their phishing attempts went past their targets' spam filters.
THE
SMOKING GUN?
None of this new data constitutes a smoking gun that can clearly frame Russia as the culprit behind the almost unprecedented hacking campaign that has hit the DNC and several other targets somewhat connected to the US presidential election.
Almost
two weeks ago, the US government took the rare step of publicly
pointing the finger at the Russian government, accusing it of
directing the recent string of hacks and data breaches. The intelligence
community declined to explain how they reached their conclusion, and it’s fair
to assume they have data no one else can see.
”They don’t want to understand the evidence.”
This
newly uncovered data paints an even clearer picture for the public, showing a
credible link between the several leaking outlets chosen by the hackers, and,
once again, pointing toward Fancy Bear, a notorious hacking group that’s widely
believed to be connected with the Russian government. While there are still naysayers,
including presidential candidate and former reality TV star Donald Trump, for
many, the debate over who hacked the DNC, and who’s behind all this hacking, is
pretty much closed.
“We are
approaching the point in this case where there are only two reasons for why
people say there’s no good evidence,” Rid told me. “The first reason is because
they don’t understand the evidence—because the don’t have the necessary
technical knowledge. The second reason is they don’t want to understand the
evidence.”
UPDATE,
10/20/2016, 4:31 p.m.: After publication of this story, Bitly sent Motherboard a statement to
say the company can only do so much to prevent malicious actors from using its
service, as it "cannot proactively police our customers’ private data without
compromising our commitment to their privacy."
"The
links and accounts related to this situation were blocked as soon as we were
informed. This is not an exploit of Bitly, but an unfortunate exploit of
Internet users through social engineering. It serves as a reminder that even
the savviest, most skeptical users can be vulnerable to opening unsolicited
emails," the statement read.
Get six
of our favorite Motherboard stories every day by signing up for our newsletter.
You can
reach us at letters@motherboard.tv.
Letters may be published. Want to see other people talking
about Motherboard? Check out our letters to the editor.
Source:
motherboard




No comments:
Post a Comment